Lumen stops 1.06 Tbps DDoS attack in the company's largest mitigation to date
Rhea-AI Summary
Lumen Technologies (NYSE: LUMN) reported its successful mitigation of a record DDoS attack, reaching 1.06 Tbps, which was part of a broader campaign targeting a single victim. Remarkably, the targeted organization experienced no downtime during this incident. The report highlighted emerging trends in cyber-attacks, including the misuse of cloud services and the increase in 'hit-and-run' tactics. Notably, attacks on VoIP protocols, specifically SIP, saw a significant rise of 315% compared to the previous quarter. This reinforces Lumen's commitment to providing robust security frameworks for its clients.
Positive
- Successfully mitigated a record DDoS attack of 1.06 Tbps, showcasing the company's capabilities.
- Target experienced no downtime despite the size and complexity of the attack.
- Emerging trends in DDoS attacks identified, indicating the company is at the forefront of threat intelligence.
Negative
- None.
News Market Reaction 1 Alert
On the day this news was published, LUMN declined 0.91%, reflecting a mild negative market reaction.
Data tracked by StockTitan Argus on the day of publication.
Intended victim experienced no downtime despite attacker's persistence
DENVER, Aug. 9, 2022 /PRNewswire/ -- In its quarterly report on Distributed Denial of Service (DDoS) attacks, Lumen Technologies (NYSE: LUMN) revealed the company mitigated one of its largest ever – a 1.06 terabits per second (Tbps) attack that was part of a larger campaign targeting a single victim. Despite the size and complexity of the attempted attack, the target experienced no downtime.
Experience the full interactive Multichannel News Release here: https://www.multivu.com/players/English/9039151-lumen-quarterly-ddos-report-q2-2022/
Size was not the only notable element of the failed attack; it was also part of a larger campaign in which the threat actor attempted to leverage multiple techniques. These techniques are called out in the report as emerging trends in the second quarter.
Read the full Q2 2022 DDoS report: https://tinyurl.com/Q2DDoSReport
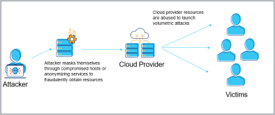
- Attackers leverage cloud-based services in a fraudulent way to significantly boost their attack capability.
- To be successful at this type of attack, cybercriminals mask their acquisition and control of cloud-based services through compromised hosts or anonymizing services. The attacker then abuses the cloud providers' resources to launch volumetric attacks against their intended victims.
- To learn how to avoid being a victim of compromised cloud services, read the full Q2 DDoS report.
"Using cloud and hosting providers to launch large DDoS attacks creates a unique challenge because it puts both the victim and the provider at risk," said Mark Dehus, director of threat intelligence for Black Lotus Labs, the threat research team at Lumen. "Cloud providers must be vigilant to ensure their services are not being abused. They should also have mitigation methodologies to limit the impact if a threat actor gains unauthorized or fraudulent access to resources."
- Analysis from Black Lotus Labs revealed the 1.06 Tbps attack was part of a larger campaign that lasted 12 minutes. It began when the threat actor attempted to deploy a series of "hit-and-run" attacks. With this technique, victims are typically targeted with a series of consecutive or concurrent attacks that are relatively small in size and duration. Threat actors deploy these attacks to assess a potential victim's defenses and determine which attack methods – if any – will be successful.
- The longest campaign Lumen mitigated in Q2 lasted 21 days, 8 hours.
- Learn how to protect against hit-and-run attacks with Lumen DDoS Mitigation services.
- Late last year, several researchers (including Lumen) began reporting on a rise in attacks targeting VoIP providers. In Q2 2022, one attack vector – Session Initiation Protocol (SIP) – stood out in the data. Although the number of SIP attacks that Lumen mitigated was relatively small – just
1.84% of all mitigations – they represented a315% increase over Q1 2022, and a475% increase over Q3 2021. - While the number of SIP attacks is low compared to tried-and-true methods, attacking SIP is considered a more surgical approach to disrupting VoIP services compared to DDoS brute-force methods like TCP-SYN flooding and UDP-based amplification. For more information about Lumen's previous research into VoIP attacks, read our Q4 2021 DDoS report.
"Organizations of all types can be victimized by DDoS attacks," said Dehus. "Using the intelligence and visibility from the Lumen Platform, Black Lotus Labs can protect Lumen DDoS customers with better insights from the ever-growing list of threats to business-critical systems and data."
- Read the full Q2 2022 DDoS report.
- Visit the Lumen Quarterly DDoS report archive.
- Learn about Lumen's comprehensive DDoS mitigation services.
Lumen is guided by our belief that humanity is at its best when technology advances the way we live and work. With approximately 450,000 route fiber miles and serving customers in more than 60 countries, we deliver the fastest, most secure platform for applications and data to help businesses, government and communities deliver amazing experiences. Learn more about the Lumen network, edge cloud, security, communication and collaboration solutions and our purpose to further human progress through technology at news.lumen.com/home, LinkedIn: /lumentechnologies, Twitter: @lumentechco, Facebook: /lumentechnologies, Instagram: @lumentechnologies and YouTube: /lumentechnologies. Lumen and Lumen Technologies are registered trademarks in the United States.
Services not available everywhere. Business customers only. Lumen may change, cancel or substitute products and services, or vary them by service area at its sole discretion without notice. ©2021 Lumen Technologies. All Rights Reserved.

![]() View original content:https://www.prnewswire.com/news-releases/lumen-stops-1-06-tbps-ddos-attack-in-the-companys-largest-mitigation-to-date-301602552.html
View original content:https://www.prnewswire.com/news-releases/lumen-stops-1-06-tbps-ddos-attack-in-the-companys-largest-mitigation-to-date-301602552.html
SOURCE Lumen Technologies








