CyberArk Launches New Capabilities for Securing Access to Cloud Workloads and Services as Part of Its Identity Security Platform
- CyberArk provides risk-based intelligent privilege controls for secure access to cloud environments
- New enhancements to CyberArk Secure Cloud Access solution
- Research shows organizations vulnerable to identity-related attacks
- None.
Only CyberArk Provides the Right Level of Intelligent Privilege Controls to Enable Secure Access to Every Layer of Cloud Environments with Zero Standing Privileges
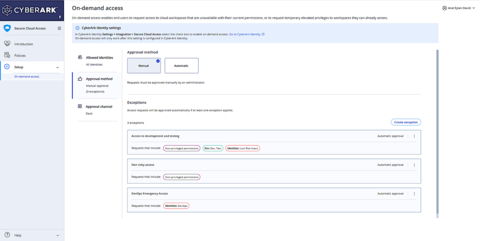
With CyberArk Secure Cloud Access users can configure context-based, automatic approval workflows to reduce the time it takes to troubleshoot critical situations. (Graphic: Business Wire)
Research shows that
“The remediation and removal of excessive, unneeded and unused permissions and entitlements from administrators, employees, service accounts and machine accounts is key to maintaining a posture of least privilege access, and our research shows that organizations are greatly challenged in this area,” said Melinda Marks, practice director, cybersecurity, Enterprise Strategy Group (ESG). “By combining greater automation and developer-focused user experience with its approach to zero standing privileges and just-in-time controls for the cloud, CyberArk is helping organizations reduce the exposure window while saving overworked cybersecurity teams from manual work.”
CyberArk Secure Cloud Access: Reducing Risk with Least Privilege and Just-in-Time Controls
Part of the CyberArk Identity Security Platform, Secure Cloud Access elevates permissions just-in-time to roles scoped for least privilege access, enabling cloud developers and administrators to maintain velocity while reducing the risks of credential theft and excessive access. New capabilities include:
- The ability to identify IAM misconfiguration risks in multi-cloud environments.
- New context-based, automatic approval workflows for high-risk access to cloud services. These workflows can be easily customized to meet governance objectives via no-code identity orchestration and automation capabilities within the CyberArk platform. Tight integration with IT Service Management (ITSM) and ChatOps tooling facilitates greater adoption from engineers and allows cloud security teams to rapidly and securely approve time-sensitive access requests in service outages. CyberArk is the only identity security vendor to offer this capability.
- Additional support for delegated administration, allowing for approvals to be addressed on a team or department level. A new integration between CyberArk Vendor Privileged Access Manager and Secure Cloud Access allows third party vendors to securely access cloud services with zero standing privileges – from the same unified platform.
- Expanded coverage for just-in-time access to support short-lived infrastructure workloads in Google Cloud Platform, enabling more multi-cloud deployments.
-
Regional datacenter coverage added in
Australia ,Canada ,UK ,Germany andIndia to meet demand for these capabilities.
“Secure Cloud Access enables us to secure our cloud with zero standing privileges and without impacting productivity,” said Jose Voisin, chief information officer, Carmeuse. “Users continue to access the cloud as always while security teams implement least privilege with on-demand and seamless elevation of privileges.”
The CyberArk Identity Security Platform features flexible, risk-based controls to secure access to different targets – for both human and non-human identities. These targets include SaaS applications, workloads and cloud services – by bots, service accounts, business users, IT admins, software developers, cloud engineers and third-party vendors.
“Cloud services have afforded organizations tremendous speed to deliver new applications, but they have also created countless new identities and new attack methods. Cybersecurity controls often lag behind the scale of these new environments – contributing to cybersecurity debt. We are delivering new cloud security solutions that emphasize automation and risk reduction to help close that gap,” said Matt Cohen, CEO, CyberArk. “CyberArk is continuously investing to deliver comprehensive, innovative cloud security solutions, like Secure Cloud Access, that help dramatically improve identity security in the cloud.”
Additional CyberArk Cloud Security Resources
Webinar: Multi-Cloud Identity Security, Combating a Wide-Open Door
eBook: 2024 Playbook: Identity Security and Cloud Compliance
1 – Enterprise Strategy Group, “The Holistic Identity Security Maturity Model: Raising the Bar for Cyber Resilience,” by Jack Poller, February 2023
About CyberArk
CyberArk (NASDAQ: CYBR) is the global leader in identity security. Centered on intelligent privilege controls, CyberArk provides the most comprehensive security offering for any identity – human or machine – across business applications, distributed workforces, hybrid cloud environments and throughout the DevOps lifecycle. The world’s leading organizations trust CyberArk to help secure their most critical assets. To learn more about CyberArk, visit https://www.cyberark.com, read the CyberArk blogs or follow on LinkedIn, Twitter, Facebook or YouTube.
Copyright © 2023 CyberArk Software. All Rights Reserved. All other brand names, product names, or trademarks belong to their respective holders.
View source version on businesswire.com: https://www.businesswire.com/news/home/20231012116354/en/
Media Contacts:
Carissa Ryan, CyberArk
Email: press@cyberark.com
Investor Relations:
Erica Smith, CyberArk
Email: ir@cyberark.com
Source: CyberArk
FAQ
What are the new capabilities announced by CyberArk?
How does CyberArk provide secure access to cloud environments?
What is the CyberArk Secure Cloud Access solution?






