Phishing Scams Take Advantage of Crypto Hype
Avast reports a surge in cryptocurrency phishing scams during the first half of 2021, targeting regions with increasing crypto adoption. The U.S., Brazil, and Nigeria are the primary targets. The rise coincides with Bitcoin's growing popularity, especially after its legalization in El Salvador. Avast warns that as cryptocurrency gains traction, it becomes more appealing to hackers. The company provides guidance on secure cryptocurrency storage and scam identification to protect users from these growing threats.
- None.
- None.
Insights
Analyzing...
PRAGUE, July 13, 2021 /PRNewswire/ -- Avast (LSE:AVST), a global leader in digital security and privacy, has observed in the first six months of 2021 that cryptocurrency-focused phishing scams are more likely to appear in countries where cryptocurrency is rising in popularity.
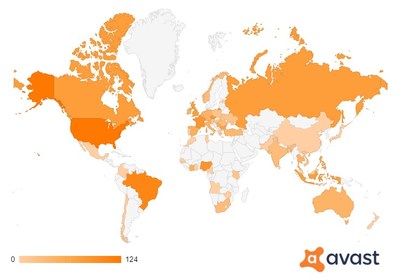
Avast's threat labs researchers have intercepted and protected users against a rise in crypto-related phishing sites since the start of the year, with the majority posing as legitimate custodial wallets. The rise of these sites is higher in countries where cryptocurrency adoption is most prevalent1. The United States, Brazil and Nigeria are the biggest targets for these crypto-scams, with notable levels of scams also in the UK, France, Russia and India. In this research, Avast Threat Labs monitored a selection of 37 samples. The global heatmap below shows where around the world users visited crypto-related phishing in the first six months of 2021:
Peter Kovac, senior researcher at Avast, said, "The crypto market is surging right now. Bitcoin has been given a boost following recent news from El Salvador that it will be recognized as legal tender in the country - with other countries in the region tipped to follow suit."
"This surge in Bitcoin is having a knock-on effect across the wider crypto space and some analysts are even predicting that 2021 will be a record-breaking year for cryptocurrencies. However, as it has grown in popularity, it has also grown as a more lucrative target for hackers - and our researchers have found the levels of crypto-related scams are most prevalent in regions where cryptocurrencies are gaining popularity."
Given its growing popularity, experts at Avast have provided advice on how to store cryptocurrencies, keep funds safe, and spot scams.
How to store cryptocurrency
There are several methods and crypto wallets that cryptocurrency owners can deploy to store their cryptocurrency. Each has its own advantages and potential security pitfalls.
Custodial wallets
With a custodial wallet, coins (cryptocurrencies) are managed by some other entity, like a cryptocurrency exchange such as Binance, or similar service. It works like a traditional bank account, where users can log in and manage their funds.
- The advantages: The burden of securing funds is partially offloaded to the service provider, users have guarantees and insurance to a certain extent.
- The risks: If the service goes bankrupt or is fraudulent it could lose some or all funds. If this happens, users are at the mercy of the service provider, and they may limit people's access to their money.
- Relevant threats: It's vital that users view their crypto account like any other form of online banking, with the same threats and vulnerabilities facing it, without the same protections and insurances that they have with traditional banks. Phishing is one of the biggest threats facing custodial wallets, with fake websites impersonating exchanges and services designed to steal people's credentials and funds popping up all the time.
Software wallets
Software wallets are applications that manage cryptocurrency owners' private keys and allow them to make transactions directly.
- The advantages: Software wallets are designed to be very convenient and easy to use. As a non-custodial wallet, people have complete control over their funds.
- The risks: The device the software wallet is stored on will be the single point of failure. If a device with the app is hacked, stolen or even damaged, then the user could lose access to their funds forever.
- Relevant threats: Besides the physical risks, ransomware encrypting the device and data stored on it, and demanding a ransom payment to unlock said device and data, pose a major threat. Trojans spying on the user's data, and backdoors letting intruders into the device, also pose a huge risk to software wallets.
Paper & brain wallets
These are the most simple solution but also the most error prone – simply having the private key written down or memorized.
- The advantages: Put simply, the advantage is its simplicity, lack of cost and will not be susceptible to hacking or other computer threats.
- The risks: If something happens to the paper such as damage or theft, or the user has a lapse in memory, they risk losing all of their funds.
- Relevant threats: There will be no backup in case of loss of paper or memory. Once it's gone, it's gone for good.
Hardware wallets
Hardware wallets are an actual separate device, such as a USB, that acts as the wallet. These wallets also come with a "recovery sheet" with the private key written on a piece of paper (or carved into steel to withstand fire and other forms of physical damage).
- The advantages: Hardware wallets are especially designed to prevent hacking. Only very select, skilled individuals have shown the ability to crack a hardware wallet after having long-term physical access to it.
- The risks: As with any physical device, losing it would be one of the biggest risks. However, providing a crypto owner is using it according to the best practices by having a secure safety pin/password, it is rather secure. While not necessarily a risk, hardware wallets can be expensive, with associated safekeeping costs.
- Relevant threats: Providing a user follows best practices, the threats are minimal. Most hardware wallets require several checks before they allow people to send money. These happen on the device and private keys never leave that device.
How to keep cryptocurrency safe
Users should be wary of scams: Scams can come in many forms online, from "crypto giveaways by Elon Musk" to "we will invest your money for you with XYZ% gains every month". If it sounds too good to be true, then it probably is.
Crypto owners should:
- Watch out for unsolicited private messages: Whether that's on WhatsApp/Telegram or any other social media forum, people should immediately block any unsolicited message that may be fraud. For example, if a message comes from an unknown number, or if it comes from a contact but is an unusual, and possibly urgent message coming from the contact, the contact's phone might have been hacked. It is recommendable to reach out to a contact, for example via phone call, and verify if they really sent this message before taking any further action. Even if the message is unrelated to crypto, the intention can be phishing, to ultimately spy on the user's data.
- Be aware of mobile phishing: Hackers are increasingly targeting people on their mobile devices in order to steal crypto credentials. These social engineering attacks can come from anywhere on a mobile device, including texts, social media, third-party messaging platforms or email. Beyond phishing, malicious mobile apps are also on the rise that have the hidden ability to log keystrokes and spy the activity on people's screens. To prevent mobile phishing attacks, users can use Avast Secure Browser, which offers an anti-phishing feature that blocks dangerous websites on Android devices. The browser's anti-phishing feature also works on Windows and Mac devices.
- Rely on services that use strong security measures: When choosing a custodial or software wallet, people should be assured to choose a provider that offers strong security measures including two-factor-authentication methods. For more security, there are also platforms that encourage the user to set up separate passwords to log in to the platform, and to do a transfer. People who want to stay entirely private may decide for a platform that does not require them to submit an ID, but oftentimes these platforms provide poor security measures. There are platforms that can offer this as they allow crypto trading only instead of trading with Fiat money such as Euro or US-Dollar, which is why they are not obliged to stick to anti-money laundering and know your customer (KYC) rules.
- Install an antivirus: Crypto owners should ensure that they have strong antivirus protection across all of their devices. For example, many people will have an antivirus on their PC but not on their mobile devices or tablets - which is why malicious mobile phishing and malware campaigns have been so effective for hackers. Crypto accounts can be worth a very significant amount of money, so for users it's essential to ensure robust internet security on any device on which crypto information is stored or from which accounts are accessed.
About Avast:
Avast (LSE:AVST), a FTSE 100 company, is a global leader in digital security and privacy. With over 435 million users online, Avast offers products under the Avast and AVG brands that protect people from threats on the internet and the evolving IoT threat landscape. The company's threat detection network is among the most advanced in the world, using machine learning and artificial intelligence technologies to detect and stop threats in real time. Avast digital security products for Mobile, PC or Mac are top-ranked and certified by VB100, AV-Comparatives, AV-Test, SE Labs and others. Avast is a member of Coalition Against Stalkerware, No More Ransom, and the Internet Watch Foundation. Visit: www.avast.com.
Keep in touch with Avast:
- Follow us on Twitter: @Avast_antivirus
- For security and privacy insights, visit the Avast blog: https://blog.avast.com/
- For handy guides, advice and tips, visit Avast Academy: https://www.avast.com/c-academy
- Join our LinkedIn community: https://www.linkedin.com/avast
- Visit our Facebook group: www.facebook.com/avast
Media Contact
pr@avast.com
1 Statista: Bitcoin trading volume on online exchanges in various countries worldwide in 2020
![]() View original content to download multimedia:https://www.prnewswire.com/news-releases/phishing-scams-take-advantage-of-crypto-hype-301331406.html
View original content to download multimedia:https://www.prnewswire.com/news-releases/phishing-scams-take-advantage-of-crypto-hype-301331406.html
SOURCE Avast Software, Inc.